/1
#Ancilia_Alerts
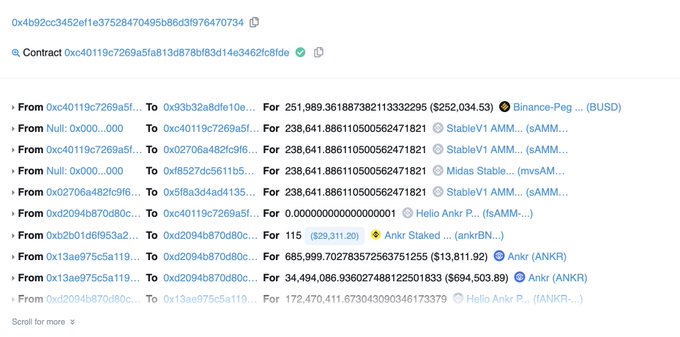
Our system detected a hack targeting:
@MidasCapitalxyz
on BSC. Hacker (0x4b92cc3452ef1e37528470495b86d3f976470734) has gained $600K+.
1
5
21
Replies
@MidasCapitalxyz
2/ Root cause analysis: contract and its implementation contract misused the redeem counter. Because of lacking source code for implementation contract 0xf3c8, this analysis is based on the on-chain code logic.
1
2
3
@MidasCapitalxyz
3/ Attached 2 screenshots. Basically storage slot 0x13 is a mapping which contains like a counter allowed for user to call redeemUnderlying(). The function mint() will set that storage after deposit(). The formula is like (1e18 * 1e18 * mint_value)/exchangeRateCurrent().
1
2
4
@MidasCapitalxyz
4/ So if you provide different amount of HAY/BUSD AMM tokens, you will get multiple times token back. It is like a free ATM. I don't understand what will be the business logic behind.
0
2
6