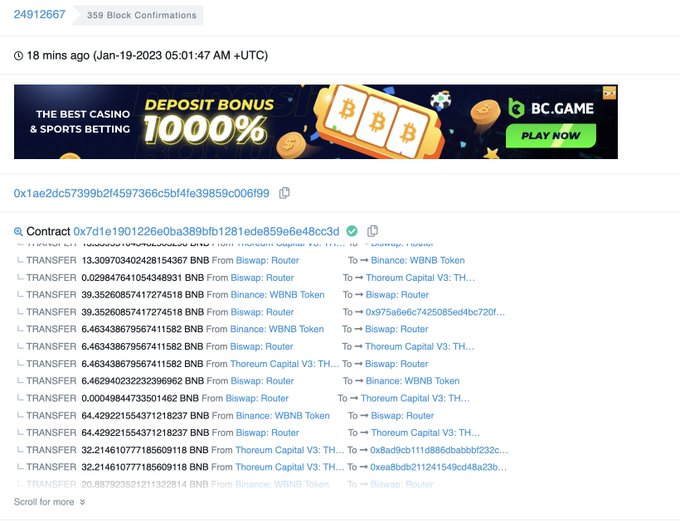
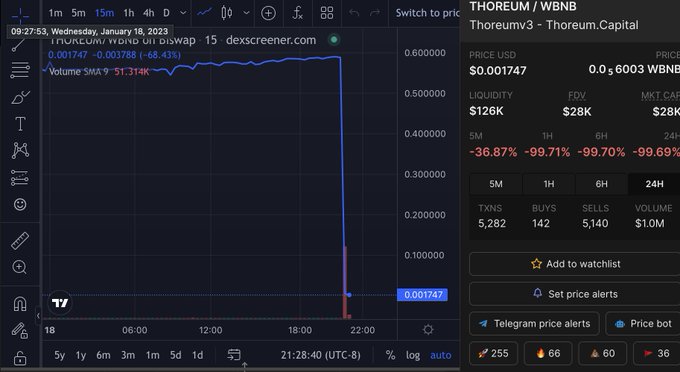
1/ We detect a hack on
@ThoreumFinance
. Hacker (0x1ae2dc57399b2f4597366c5bf4fe39859c006f99) has gained ~2000 BNB and deposited to tornado (via 0x1285fe345523f00ab1a66acd18d9e23d18d2e35c).
#Web3
#Hacking
3
5
18
Replies
@ThoreumFinance
2/ we think the root cause is in the "transfer" func. In the Tx, when 0x7d1e1901226e0ba389bfb1281ede859e6e48cc3d calls transfer to itself, its balance will increase. By repeating doing this, it ends with 500k+ $THOREUM tokens
1
0
4
@ThoreumFinance
3/ in the same tx, all gained $THOREUM tokens are swapped to WBNB and send to 0x1285fe345523f00ab1a66acd18d9e23d18d2e35c, which later deposit into Tornado. Since no source code is verified, the analysis is based on our Akkala emulator.
1
1
2
@ThoreumFinance
4/ the problematic contract implementation (0x79fe086a4c03c5e38ff8074dea9ee0a18dc1af4f) was created and used (i.e., upgrade proxy's implementation) by "Thoreum: Deployer" (0x6a963573b9a7aaef9cb9eee747e1b6b2c21b0520) ~2 hours ago.
1
2
4